SIBERXCON
This executive cybersecurity conference brings together leaders from AI, cybersecurity, government, and academia for a full program focused on AI-driven security risk, emerging cyber threats, and the decisions shaping the future of digital trust.
Through a curated mix of executive discussions, applied workshops, live demonstrations, and innovation zones highlighting emerging startups and research, SiberXCon provides sponsors with meaningful engagement and direct access to enterprise buyers, policymakers, researchers, and industry leaders in a high-trust, limited-attendance environment.
FOUR FLAGSHIP
EXPERIENCES



in Cybersecurity

GOVERNING COMMITTEE
SCHEDULE
- May 25, 2026 8:00 AM - 8:55 AMRegistration{ "name":"siberXcon - Registration", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"08:00", "endTime":"08:55", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Enjoy our seamless checkin process and grab your information for the day. We have a fresh selection of breakfast selections available to you right after.
- May 25, 2026 8:00 AM - 8:55 AMBreakfast{ "name":"siberXcon - Breakfast", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"08:00", "endTime":"08:55", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Begin your morning with a healthy and inspired breakfast.
Chef's Selection of Seasonal Juice & Smoothies
Cereals | Whole & Skim Milk
Quinoa, Nut & Dried Fruit Granola
Natural & Fruit Flavoured Yogurts
Fruit & Berry Salad
Danish Pastries , Assorted Muffins, Croissants, Mini Bagels,
Sourdough, White & Multigrain Breads
Sweet Butter, Fruit Marmalade , Preserves & Honey
Plain & Fine Herbs & Garlic Cream Cheese
Steel Cut Oatmeal Bar
Brown Sugar, Raisins, Cinnamon , Pecans & Pure Maple Syrup
Classic Scrambled Egg
Cheddar Cheese & Chives | NF, GF, Veg - May 25, 2026 8:55 AM - 9:05 AMWelcome and Opening{ "name":"siberXcon - Welcome and Opening", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"08:55", "endTime":"09:05", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Join us as we begin with our land acknowledgements and opening comments from dignitaries and special guests.
- May 25, 2026 9:05 AM - 9:30 AMAI-Driven Cyber Threat Intelligence: Beyond Traditional SIEM{ "name":"siberXcon - AI-Driven Cyber Threat Intelligence: Beyond Traditional SIEM", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"09:05", "endTime":"09:30", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Explore how AI is revolutionizing cyber threat intelligence, shifting beyond traditional SIEM tools to proactive defense strategies.
- May 25, 2026 9:30 AM - 10:10 AMPost-Quantum Cryptography Readiness: AI's Role in Secure Migration{ "name":"siberXcon - Post-Quantum Cryptography Readiness: AI's Role in Secure Migration", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"09:30", "endTime":"10:10", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Discuss the critical role of AI in preparing for a post-quantum world and its impact on secure migration in the cryptography field.
- May 25, 2026 10:10 AM - 10:40 AMCoffee & Snack Break{ "name":"siberXcon - Coffee & Snack Break", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"10:10", "endTime":"10:40", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Recharge with a tasty snack break!
Almond Butter Protein Bar
Ontario Apple Oat Bar
Indulgent Energy Bar
Dark Chocolate, Raspberry & Crispy Rice
Acai Bowl
Mixed Berry Smoothie, Vanilla Yogurt, Mango
Hemp Seeds & Chia | NF, GF, V
Fruit Skewers
Mango Passion Fruit Cold Pressed Juice
Freshly brewed regular & decaffeinated Coffee & Teas. - May 25, 2026 10:40 AM - 11:20 AMAI in Red Teaming: Automating Attack Simulations & Defense Testing{ "name":"siberXcon - AI in Red Teaming: Automating Attack Simulations & Defense Testing", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"10:40", "endTime":"11:20", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Delve into how AI is enhancing red teaming by automating attack simulations and defense testing, providing a more efficient and accurate assessment of security systems.
- May 25, 2026 10:40 AM - 11:20 AMAI-Driven Automation for Incident Detection and Response{ "name":"siberXcon - AI-Driven Automation for Incident Detection and Response", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"10:40", "endTime":"11:20", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Examine how AI can automate the detection of cyber incidents and improve response times, minimizing human error and reaction delays.
- May 25, 2026 10:40 AM - 11:20 AMAI for Cryptographic Key Management in a Hybrid Cloud Environment{ "name":"siberXcon - AI for Cryptographic Key Management in a Hybrid Cloud Environment", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"10:40", "endTime":"11:20", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Learn how AI is strengthening cryptographic key management in hybrid cloud environments to ensure data security.
- May 25, 2026 11:20 AM - 11:35 AMWellness Break{ "name":"siberXcon - Wellness Break", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"11:20", "endTime":"11:35", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Stretch your legs and take a deep breath!
- May 25, 2026 11:35 AM - 12:15 PMAI-Enhanced Blockchain Security: Protecting Decentralized Systems{ "name":"siberXcon - AI-Enhanced Blockchain Security: Protecting Decentralized Systems", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"11:35", "endTime":"12:15", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Understand how AI can enhance blockchain security, focusing on protecting decentralized systems from emerging threats.
- May 25, 2026 11:35 AM - 12:15 PMSupply Chain Cybersecurity: AI for Threat Prediction & Incident Response{ "name":"siberXcon - Supply Chain Cybersecurity: AI for Threat Prediction & Incident Response", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"11:35", "endTime":"12:15", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Discuss how AI is used in predicting threats and responding to incidents within supply chains to protect businesses from interconnected vulnerabilities.
- May 25, 2026 11:35 AM - 12:15 PMLeveraging AI for Real-Time Threat Intelligence in Cloud Security{ "name":"siberXcon - Leveraging AI for Real-Time Threat Intelligence in Cloud Security", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"11:35", "endTime":"12:15", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Explore how AI provides real-time threat intelligence to enhance cloud security, responding to vulnerabilities faster than traditional methods.
- May 25, 2026 12:15 PM - 1:10 PMLunch{ "name":"siberXcon - Lunch", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"12:15", "endTime":"13:10", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Refuel and re-energize with a warm lunch
Caesar Salad
Coast to Coast Seafood Corn Chowder, PEI Potatoes, Mussels,
Pan Seared Salmon
Roasted Chicken
Montreal Spiced Rub Brisket
Warm Red Skin Potato Salad
Seasonal Roasted Vegetable Medley
Chocolate Mousse
Warm Ontario Apple Crumble Tart
Citrus Puff Tart - May 25, 2026 1:10 PM - 1:30 PMThe Future of AI and Human Collaboration in Cyber Defense: Beyond Automation{ "name":"siberXcon - The Future of AI and Human Collaboration in Cyber Defense: Beyond Automation", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"13:10", "endTime":"13:30", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Explore how AI and human expertise will work together in the future of cyber defense, blending human intuition with AI-driven automation to enhance strategic decision-making.
- May 25, 2026 1:30 PM - 2:10 PMNavigating the Dark Side: AI in Cybercrime and Ethical Dilemmas{ "name":"siberXcon - Navigating the Dark Side: AI in Cybercrime and Ethical Dilemmas", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"13:30", "endTime":"14:10", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
A thought-provoking panel on the growing use of AI in cybercrime. Experts will discuss how malicious actors are leveraging AI for attacks, the ethical challenges this presents, and what cybersecurity professionals can do to stay ahead.
- May 25, 2026 2:10 PM - 2:30 PMAI and the Future of Cybersecurity Governance: How Machine Learning Will Shape Global Standards{ "name":"siberXcon - AI and the Future of Cybersecurity Governance: How Machine Learning Will Shape Global Standards", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"14:10", "endTime":"14:30", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Learn how AI-driven models will influence the development of global cybersecurity standards, shaping the future of regulations and frameworks to address emerging digital threats
- May 25, 2026 2:30 PM - 3:10 PMCoffee & Snack Break{ "name":"siberXcon - Coffee & Snack Break", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"14:30", "endTime":"15:10", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Recharge with a tasty snack break!
Vanilla & Chocolate Marbled Mini Cake
Lemon Mini Cake
Spicy Honey Mini Cake
Classic Opera Chocolate And Coffee Cake
Fruit Skewers
Raspberry Lemonade With Mint
Freshly brewed regular & decaffeinated Coffee & Teas. - May 25, 2026 3:10 PM - 3:50 PMAI-Driven Automation for Vulnerability Management{ "name":"siberXcon - AI-Driven Automation for Vulnerability Management", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"15:10", "endTime":"15:50", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Learn how AI automates vulnerability management, identifying and patching weaknesses in systems before they can be exploited.
- May 25, 2026 3:10 PM - 3:50 PMAutomating Cybersecurity Compliance: AI for NIST, ISO and SOC 2 Mapping{ "name":"siberXcon - Automating Cybersecurity Compliance: AI for NIST, ISO and SOC 2 Mapping", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"15:10", "endTime":"15:50", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Discover how AI can simplify compliance with cybersecurity frameworks such as NIST, ISO, and SOC 2, ensuring accurate and timely mapping.
- May 25, 2026 3:10 PM - 3:50 PMAI for Privacy and Data Protection Compliance: Navigating GDPR & CCPA{ "name":"siberXcon - AI for Privacy and Data Protection Compliance: Navigating GDPR & CCPA", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"15:10", "endTime":"15:50", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Learn about AI's role in helping organizations navigate and comply with complex privacy regulations such as GDPR and CCPA.
- May 25, 2026 3:50 PM - 4:05 PMWellness Break{ "name":"siberXcon - Wellness Break", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"15:50", "endTime":"16:05", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Stretch your legs and take a deep breath!
- May 25, 2026 4:05 PM - 4:45 PMAI at the C-Suite Level; Strategy, Risk, and Opportunity{ "name":"siberXcon - AI at the C-Suite Level; Strategy, Risk, and Opportunity", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"16:05", "endTime":"16:45", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
A high-level executive discussion on how AI is transforming business strategy, cybersecurity, and risk management; focusing on leadership, governance, and competitive advantage at the C-suite level.
- May 25, 2026 6:00 PM - 6:30 PMRegistration{ "name":"siberXcon - Registration", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"18:00", "endTime":"18:30", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Check in, grab your badge, and jump into the buzz—networking kicks off right away!
- May 25, 2026 6:30 PM - 6:35 PMDoors Open & Welcome{ "name":"siberXcon - Doors Open & Welcome", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"18:30", "endTime":"18:35", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
Step into an electrifying atmosphere as the doors open! Check in at registration, connect with peers, grab a drink, and get ready for an evening filled with energy, insight, and inspiration. This is where cybersecurity minds meet — and the conversations begin.
- May 25, 2026 6:35 PM - 10:00 PMThe Cyber Stage: Unfiltered{ "name":"siberXcon - The Cyber Stage: Unfiltered", "description":"https://siberx.org/", "startDate":"2026-05-25", "startTime":"18:35", "endTime":"22:00", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
An open-mic style session featuring raw, unfiltered talks from cybersecurity professionals and community voices. Hear real stories, lessons, and bold perspectives straight from the frontlines. No slides, no scripts — just honest conversations, insights, and a few surprises along the way.
- May 26, 2026 8:00 AM - 8:55 AMRegistration & Breakfast{ "name":"siberXcon - Registration & Breakfast", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"08:00", "endTime":"08:55", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 8:55 AM - 9:30 AMThe Evolving Threat Landscape{ "name":"siberXcon - The Evolving Threat Landscape", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"08:55", "endTime":"09:30", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 9:30 AM - 10:10 AMYour Health, Technology, and Cybersecurity: Benefits and Challenges{ "name":"siberXcon - Your Health, Technology, and Cybersecurity: Benefits and Challenges", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"09:30", "endTime":"10:10", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 10:10 AM - 10:40 AMCoffee & Snack Break{ "name":"siberXcon - Coffee & Snack Break", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"10:10", "endTime":"10:40", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 10:40 AM - 11:20 AMBreakout A | Threat Casting and Future Casting: Anticipating and Mitigating Future Cyber Threats{ "name":"siberXcon - Breakout A | Threat Casting and Future Casting: Anticipating and Mitigating Future Cyber Threats", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"10:40", "endTime":"11:20", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 10:40 AM - 11:20 AMBreakout B| Youth are the Future: Engaging Youth and Breaking Down Preconceived Notions of the CISO Role{ "name":"siberXcon - Breakout B| Youth are the Future: Engaging Youth and Breaking Down Preconceived Notions of the CISO Role", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"10:40", "endTime":"11:20", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 10:40 AM - 11:20 AMBreakout C| Fast, Autonomous, and Smarter than Ever: The Future of Identity Security{ "name":"siberXcon - Breakout C| Fast, Autonomous, and Smarter than Ever: The Future of Identity Security", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"10:40", "endTime":"11:20", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 10:40 AM - 11:20 AMBreakout D! Achieving Work-Life Balance in Cybersecurity: Navigating Demands and Responsibilities{ "name":"siberXcon - Breakout D! Achieving Work-Life Balance in Cybersecurity: Navigating Demands and Responsibilities", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"10:40", "endTime":"11:20", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 10:40 AM - 11:20 AMClosed-Door Roundtable | How Protected Are You?{ "name":"siberXcon - Closed-Door Roundtable | How Protected Are You?", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"10:40", "endTime":"11:20", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 11:20 AM - 11:35 AMWellness Break{ "name":"siberXcon - Wellness Break", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"11:20", "endTime":"11:35", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 11:35 AM - 12:15 PMBreakout A | Securing by Design: Building Trustworthy Products and Services{ "name":"siberXcon - Breakout A | Securing by Design: Building Trustworthy Products and Services", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"11:35", "endTime":"12:15", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 11:35 AM - 12:15 PMBreakout B | Unlocking Secrets: Your Essential Guide to Harnessing Privacy and Security in the Digital Age{ "name":"siberXcon - Breakout B | Unlocking Secrets: Your Essential Guide to Harnessing Privacy and Security in the Digital Age", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"11:35", "endTime":"12:15", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 11:35 AM - 12:15 PMBreakout C | H2Oh-No!: Can You Protect the Water Grid?{ "name":"siberXcon - Breakout C | H2Oh-No!: Can You Protect the Water Grid?", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"11:35", "endTime":"12:15", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 11:35 AM - 12:15 PMBreakout D | Identifying Allies for Women in Cybersecurity: Navigating Support Systems{ "name":"siberXcon - Breakout D | Identifying Allies for Women in Cybersecurity: Navigating Support Systems", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"11:35", "endTime":"12:15", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 11:35 AM - 12:15 PMClosed-Door Roundtable | Navigating Leaves in the Workplace{ "name":"siberXcon - Closed-Door Roundtable | Navigating Leaves in the Workplace", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"11:35", "endTime":"12:15", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 12:15 PM - 1:10 PMLunch{ "name":"siberXcon - Lunch", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"12:15", "endTime":"13:10", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 1:10 PM - 1:30 PMEmpowering Future Women Leaders: Overcoming Stigmas, Insecurities, and Roadblocks to Nurture Success{ "name":"siberXcon - Empowering Future Women Leaders: Overcoming Stigmas, Insecurities, and Roadblocks to Nurture Success", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"13:10", "endTime":"13:30", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 1:30 PM - 2:10 PMComparative Analysis of Cybersecurity Regulatory Compliance Across Canada, US, and UK{ "name":"siberXcon - Comparative Analysis of Cybersecurity Regulatory Compliance Across Canada, US, and UK", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"13:30", "endTime":"14:10", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 2:10 PM - 2:30 PMAttack Rewind: Deep-Dive into Modernized Legacy Exploits{ "name":"siberXcon - Attack Rewind: Deep-Dive into Modernized Legacy Exploits", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"14:10", "endTime":"14:30", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 2:30 PM - 3:10 PMCoffee & Snack Break{ "name":"siberXcon - Coffee & Snack Break", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"14:30", "endTime":"15:10", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 3:10 PM - 3:50 PMBreakout A | Cybersecurity Contributions to ESG Reports: Integrating Security into Corporate Governance{ "name":"siberXcon - Breakout A | Cybersecurity Contributions to ESG Reports: Integrating Security into Corporate Governance", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"15:10", "endTime":"15:50", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 3:10 PM - 3:50 PMBreakout B | Geopolitical Cybersecurity: Insights from Canadian Security Intelligence Service{ "name":"siberXcon - Breakout B | Geopolitical Cybersecurity: Insights from Canadian Security Intelligence Service", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"15:10", "endTime":"15:50", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 3:10 PM - 3:50 PMBreakout C | Fast, Autonomous, and Smarter than Ever: The Future of Identity Security{ "name":"siberXcon - Breakout C | Fast, Autonomous, and Smarter than Ever: The Future of Identity Security", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"15:10", "endTime":"15:50", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 3:10 PM - 3:50 PMBreakout D | The realities of cyber insurance in Canada{ "name":"siberXcon - Breakout D | The realities of cyber insurance in Canada", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"15:10", "endTime":"15:50", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 3:10 PM - 3:50 PMClosed-Door Roundtable | What to do when...{ "name":"siberXcon - Closed-Door Roundtable | What to do when...", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"15:10", "endTime":"15:50", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 3:50 PM - 4:05 PMWellness Break{ "name":"siberXcon - Wellness Break", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"15:50", "endTime":"16:05", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 4:05 PM - 4:45 PMBreakout A | AI in the Workplace: Do Your Employees Know the Rules?{ "name":"siberXcon - Breakout A | AI in the Workplace: Do Your Employees Know the Rules?", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"16:05", "endTime":"16:45", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 4:05 PM - 4:45 PMBreakout B | Beyond the Metrics: Tackling DEI Challenges in Cyber Governance{ "name":"siberXcon - Breakout B | Beyond the Metrics: Tackling DEI Challenges in Cyber Governance", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"16:05", "endTime":"16:45", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 4:05 PM - 4:45 PMBreakout C | Bots, Scripts & Non-Human Threats: Protecting APIs & Automation Platforms{ "name":"siberXcon - Breakout C | Bots, Scripts & Non-Human Threats: Protecting APIs & Automation Platforms", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"16:05", "endTime":"16:45", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 4:05 PM - 4:45 PMBreakout D | Achieving Work-Life Balance in Cybersecurity: Navigating Demands and Responsibilities{ "name":"siberXcon - Breakout D | Achieving Work-Life Balance in Cybersecurity: Navigating Demands and Responsibilities", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"16:05", "endTime":"16:45", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 4:05 PM - 4:45 PMClosed-Door Roundtable | How Protected Are You?{ "name":"siberXcon - Closed-Door Roundtable | How Protected Are You?", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"16:05", "endTime":"16:45", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 26, 2026 6:00 PM - 9:30 PMGala Award Ceremony & Cocktail Reception{ "name":"siberXcon - Gala Award Ceremony & Cocktail Reception", "description":"https://siberx.org/", "startDate":"2026-05-26", "startTime":"18:00", "endTime":"21:30", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 27, 2026 8:00 AM - 8:30 AMRegistration{ "name":"siberXcon - Registration", "description":"https://siberx.org/", "startDate":"2026-05-27", "startTime":"08:00", "endTime":"08:30", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 27, 2026 8:00 AM - 9:30 AMAct I – Reality Check{ "name":"siberXcon - Act I – Reality Check", "description":"https://siberx.org/", "startDate":"2026-05-27", "startTime":"08:00", "endTime":"09:30", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 27, 2026 9:30 AM - 11:00 AMAct II – Decision Under Pressure{ "name":"siberXcon - Act II – Decision Under Pressure", "description":"https://siberx.org/", "startDate":"2026-05-27", "startTime":"09:30", "endTime":"11:00", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 27, 2026 11:15 AM - 1:00 PMAct III – The Cyber Range{ "name":"siberXcon - Act III – The Cyber Range", "description":"https://siberx.org/", "startDate":"2026-05-27", "startTime":"11:15", "endTime":"13:00", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 27, 2026 1:00 PM - 2:30 PMAct IV – Resolution & Lunch{ "name":"siberXcon - Act IV – Resolution & Lunch", "description":"https://siberx.org/", "startDate":"2026-05-27", "startTime":"13:00", "endTime":"14:30", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
- May 27, 2026 2:30 PM - 4:30 PMAct V – Lessons Learned & Playbooks{ "name":"siberXcon - Act V – Lessons Learned & Playbooks", "description":"https://siberx.org/", "startDate":"2026-05-27", "startTime":"14:30", "endTime":"16:30", "location":"", "options":[ "Google", "Outlook.com", "Apple", "Yahoo", "iCal" ], "timeZone":"America/Toronto", "iCalFileName":"Calendar", "inline":true, "trigger":"click" }
TICKETS
Total Access
AiSecCon (May 25)
Cyber Meetup (May 25)
Canadian Women in Cybersecurity + Gala Dinner (May 26)
Now//AI (May 27)
All Meals (Hot Breakfast, Hot Lunch, Snacks) included for all three days
Restriction: Director-level & Above Security Practitioner
AiSecCon (May 25)
Cyber Meetup (May 25)
Hot Breakfast, Hot Lunch, and Snack breaks included
Restriction: Director-level & Above practitioners only
Cyber Meetup (May 25)
Full Access to Canadian Women in Cybersecurity (May 26)
Hot Breakfast, Hot Lunch, and Snack breaks included
Gala Dinner & Awards Ceremony (May 26)
For leaders who value meaningful recognition and high-calibre connections
Cyber Meetup (May 25)
Full Access to Canadian Women in Cybersecurity (May 26)
Hot Breakfast, Hot Lunch, and Snack breaks included
For professionals investing in a full day of leadership, learning, and community (excludes Gala)
Cyber Meetup (May 25)
Now//AI Workshop by SANS x siberX (May 27)
Deep-dive technical training and AI security sessions
Hot Breakfast, Lunch, and Snack breaks included
Restriction: Director-level & Above practitioners only
Cyber Meetup (May 25)
Cash Bar Available
Perfect for those looking to network in a casual setting
Cyber Meetup (May 25)
Breakouts & Workshops @ Canadian Women in Cybersecurity (May 26)
Full Day of Networking, Mentorship, and Resume/LinkedIn Reviews
Professional Headshots Included
Note: Valid Student ID required; No meals, main session or gala access
Spots.
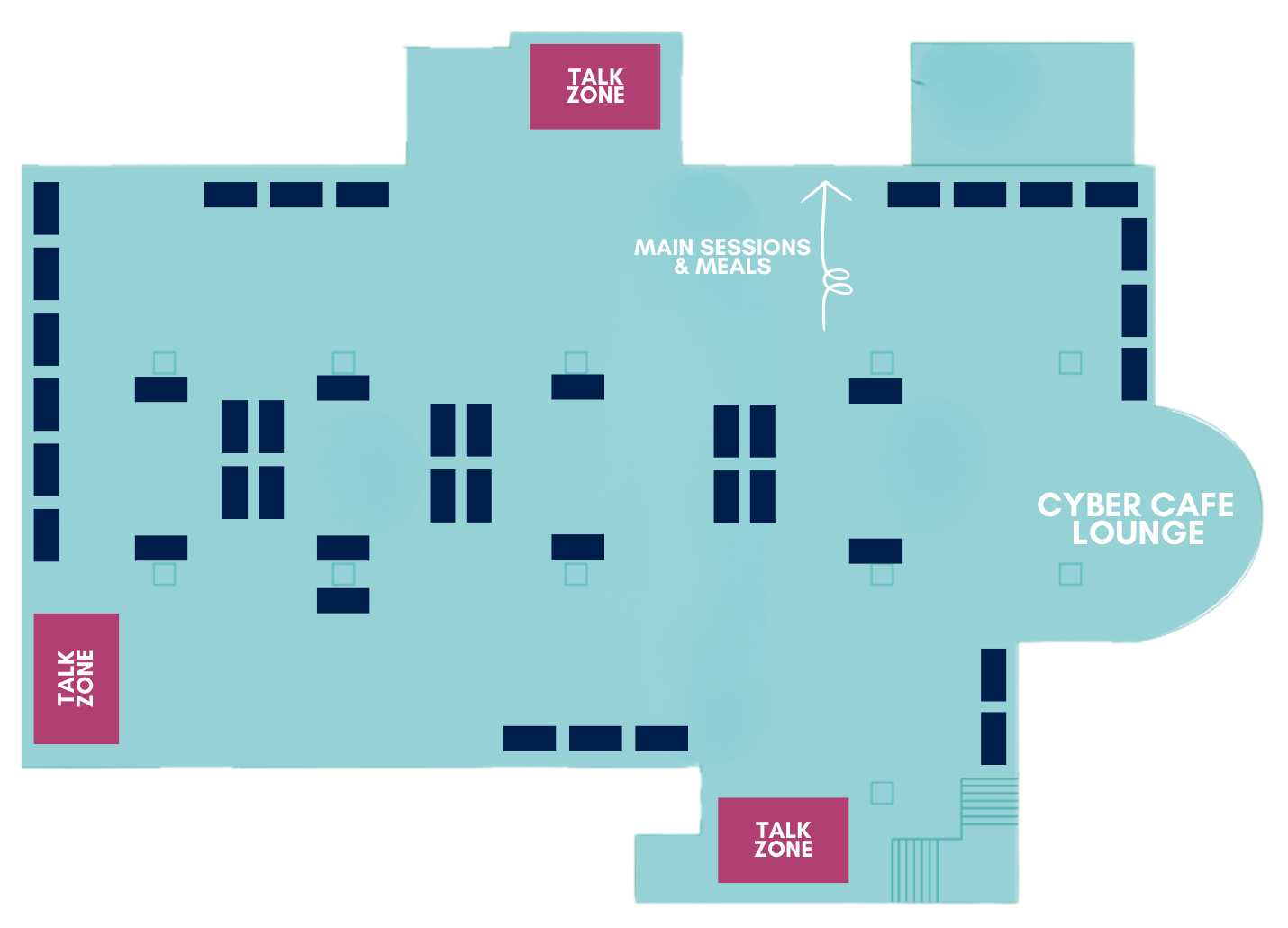
Not ready to pick a spot yet? Contact us
HYATT REGENCY
TORONTO
Toronto, ON M5V 1J9
Canada
- May 25 – 27, 2026
- Hyatt Regency Toronto
- Downtown Toronto, King West
- Steps from St. Andrew Station




























